IBL News | New York
Three researchers discovered multiple security failings in the Coursera platform, used by 82 million learners and hundreds of Fortune 500 companies.
Those vulnerabilities on the API (Application Programming Interface) were fixed by Coursera’s tech team, once the company was informed last year.
Yesterday, Thursday, July 8, the Checkmarx Security Research Team published a report on its finding.
“Through our research, we discovered multiple API issues, such as user/account enumeration via the reset password feature, lack of resources limiting on both a GraphQL and REST API, and a GraphQL misconfiguration,” wrote Erez Yalon, Head of the Security Research Group at Checkmarx.
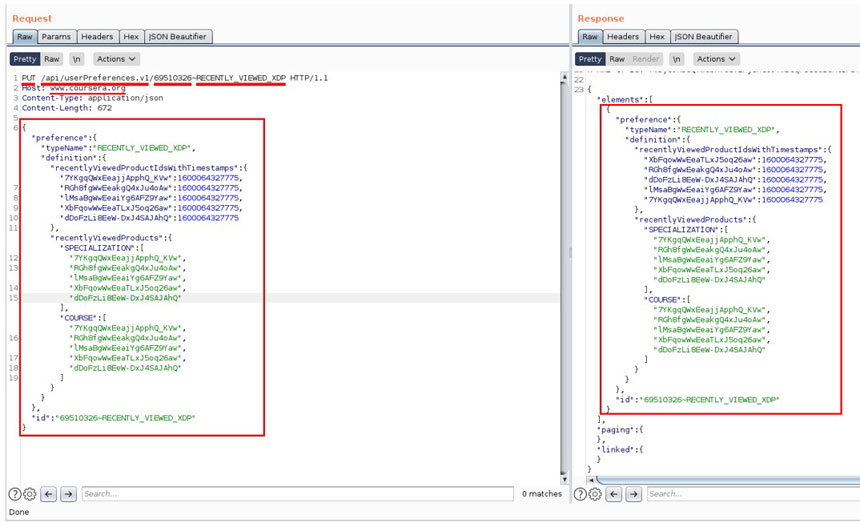
“But specifically, the Broken Object Level Authorization (BOLA) issue we found perfectly fits Coursera’s access control concerns,” he added.
The main issue of Broken Object Level Authorization (BOLA) security flaw is considered by OWASP to be a major threat due to the ease of exploitation.
BOLA flaws in APIs may expose endpoints that handle object identifiers, potentially opening the door to wider attacks.
“This vulnerability could have been abused to understand general users’ courses preferences at a large scale, but also to somehow bias users’ choices, since manipulating their recent activity affected the content rendered on Coursera’s homepage for a specific user,” Erez Yalon stated.
Meanwhile, Coursera told ZDNet that “the privacy and security of learners on Coursera is a top priority.” “We’re grateful to Checkmarx for bringing the low-risk API-related issues to the attention of our security team last year, who were able to address and resolve the issues promptly.”

 En Español
En Español